We are always eager to meet fresh talents, so check out our careers page.

We turn those challenges into peace of mind. With us, experience tailored strategies that not only secure but empower your digital journey. You're not alone; together, we make cybersecurity a stronghold of your success.

Successful Customers
Projects Delivered
Countries Portfolio
It's your robust shield against the complex landscape of cyber threats. Dive into the security of your Web, Mobile, and Network Apps with our tailored VA/PT Audits, where vulnerabilities are not just identified but transformed into strengths.
Learn moreNavigating the complexities of data security? Step into a world where compliance and security converge seamlessly. Our bespoke ISO implementation strategies are your ally in global data protection, ensuring every bit of information is shielded.
Learn moreOur tailored HIPAA & HITRUST solutions turn regulatory challenges into a stronghold of trust and integrity in patient data handling.
Learn moreAs the digital landscape evolves, so do challenges in establishing trust. Our SOC 2 solutions are not just about meeting criteria but exceeding expectations, engraving trust and reliability in every digital interaction.
Learn moreWhen cyber incidents strike, clarity and swift action are paramount. Dive into a service where intricate digital puzzles are unraveled, and actionable insights emerge to fortify your cyber terrain against future attacks.
Learn moreFeel like unseen vulnerabilities lurk in the shadows? Our Third Eye Audit illuminates the hidden, transforming uncertainties into actionable strategies, elevating your security from robust to invincible.
Learn moreAmidst the ceaseless cyber chatter, our SOC stands as your unwavering sentinel. Experience a fusion of technology and expertise that doesn’t just watch but anticipates and counters threats before they manifest.
Learn moreIt’s your robust shield against the complex landscape of cyber threats. Dive into the security of your Web, Mobile, and Network Apps with our tailored VA/PT Audits, where vulnerabilities are not just identified but transformed into strengths.
Learn moreNavigating the complexities of data security? Step into a world where compliance and security converge seamlessly. Our bespoke ISO implementation strategies are your ally in global data protection, ensuring every byte of information is shielded.
Learn moreOverwhelmed by the stringent healthcare data protection mandates? We simplify and personalize the journey. Our tailored HIPAA & HITRUST solutions turn regulatory challenges into a testament of trust and integrity in patient data handling.
Learn moreAs the digital landscape evolves, so do challenges in establishing trust. Our SOC 2 solutions are not just about meeting criteria but exceeding expectations, engraving trust and reliability in every digital interaction.
Learn moreWhen cyber incidents strike, clarity and swift action are paramount. Dive into a service where intricate digital puzzles are unraveled, and actionable insights emerge to fortify your cyber terrain against future attacks.
Learn moreFeel like unseen vulnerabilities lurk in the shadows? Our Third Eye Audit illuminates the hidden, transforming uncertainties into actionable strategies, elevating your security from robust to invincible.
Learn moreAmidst the ceaseless cyber chatter, our SOC stands as your unwavering sentinel. Experience a fusion of technology and expertise that doesn’t just watch but anticipates and counters threats before they manifest.
Learn morePioneering excellence, Briskinfosec stands as a beacon of cybersecurity innovation trusted by industry giants worldwide.
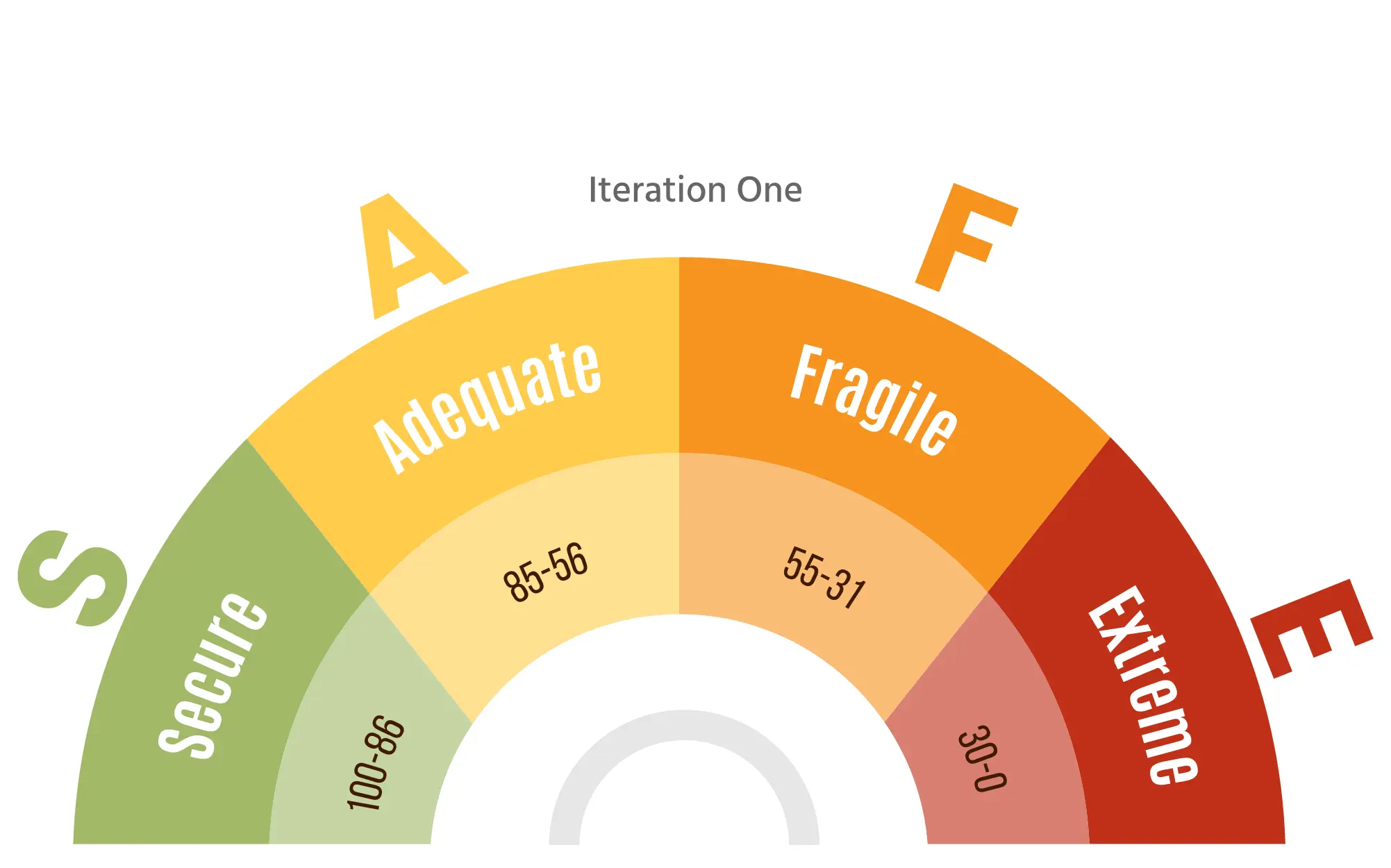
bSAFE provides a comprehensive maturity score for your web application security, aligning with OWASP ASVS standards to guide improvements and ensure continuous security enhancement.
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.


Explore our cybersecurity webinar hub! Enhance your skills, stay updated on trends, and connect with professionals through our expert-led sessions and event highlights.
Cybercrime never sleeps, and neither do we. The April 2025. Threatsploit Adversary Report is here, breaking down the 30 most shocking cyberattacks that shook industries this month.
Read moreWelcome to our March Threatsploit Adversary Report. The world of cybersecurity never stands still. Every month, new threats emerge, targeting businesses, individuals, and critical systems in increasingly creative ways.
Read moreWelcome to our February 2025 edition of the Threatsploit Adversary Report! In this report, we examine the ever-changing landscape of cyber threats, reveal new attack methods, and provide key insights into the latest developments. This is not just another news update; it’s your guide to understanding what’s happening in cybersecurity and staying aware of the evolving risks.
Read moreCelebrating our achievements and collaborations, shaping a future of excellence.
Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
The healthcare industry faces an escalating cyber crisis. Ransomware attacks are rising, with hospitals frequently experiencing breaches that disrupt patient care.
Read the blogAs organizations strive for excellence in today’s competitive landscape, compliance has become a cornerstone of success.
Read the blogRansomware has emerged as one of the most dangerous and persistent threats in the cybersecurity landscape.
Read the blogOur team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free AppointmentBriskinfosec warmly welcomes you to reach out to us through our online contact form.
We are specialized in cybersecurity solutions, GRC consultants, software development solutions, and comprehensive technology services across various domains.
We value your inquiries and anticipate providing assistance. Our team is here to help whether you're seeking an initial consultation or have any questions about our services. Get in touch with us today.
We are always eager to meet fresh talents, so check out our careers page.

Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.